Summary
- Scammers spoof your email address to bypass spam filters and appear legitimate.
- Email providers use SPF and DMARC to combat fake email addresses, but scammers still find ways around it.
- To combat spoofed emails, be cautious, use spam filtering, and consider alternate email providers.
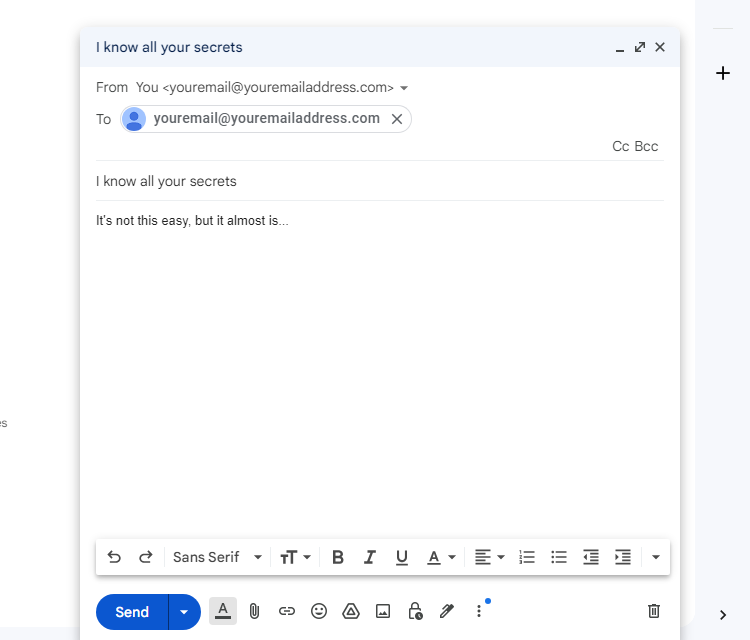
Have you ever opened an email only to find it’s spam or blackmail that seemed to come from your own email address? You’re not alone. The good news is that the hacker most likely doesn’t have access to your data. Instead, they use a trick known as “spoofing” to fake your email.
How Spammers Spoof Your Email Address
Spoofing is the act of forging an email address so that it appears to be from someone other than the person who sent it. Often, spoofing is used to trick you into thinking an email came from someone you know or a business you work with, like a bank or other financial service.
Unfortunately, email spoofing is easy. Email systems don’t always have enough security checks in place to ensure the email address you type in the “From” field truly belongs to you. It’s a lot like an envelope you put in the mail. You can write anything you want in the return address spot if you don’t care that the post office won’t be able to return the letter to you. The post office has no way of knowing whether you really live at the return address you wrote on the envelope.
Email forging works similarly. Some online services, like Outlook, pay attention to the “From” address when you send an email, preventing you from sending one with a forged address. However, other tools let you fill in anything you want. It’s as easy as creating your own email (SMTP) server. All a scammer needs is your email address, which they can buy from a data breach that contains it.
Why Do Scammers Spoof Your Address?
Scammers send you emails that appear to come from your address for one of two reasons generally. The first is in the hopes they will bypass your spam protection. If you send yourself an email, you’re likely trying to remember something important and wouldn’t want that message labeled as spam.
By using your own address, scammers hope that the built-in spam filter won’t notice and that their message will go through. Tools do exist to identify an email sent from a domain other than the one it claims to be from. However, your email provider must implement these countermeasures.
The second reason scammers spoof your email address is to gain a sense of legitimacy. It’s not uncommon for a spoofed email to claim your account is compromised. That “you sent yourself this email” serves as proof of the “hacker’s” access. They might even include a password or phone number pulled from a breached database as further proof, a trick you shouldn’t fall for.
The scammer usually then claims to have compromising information about you or pictures taken from your webcam. They then threaten to release the data to your closest contacts unless you pay a ransom. It sounds believable at first; after all, they seem to have access to your email account. But that’s the point—the scammer is faking evidence, and they most likely don’t have anything on you.
What Email Services Do to Combat the Problem
The fact that anyone can fake a return email address so easily isn’t a new problem. Plus, email providers don’t want to annoy you with spam, so they use a few technologies to combat the issue.
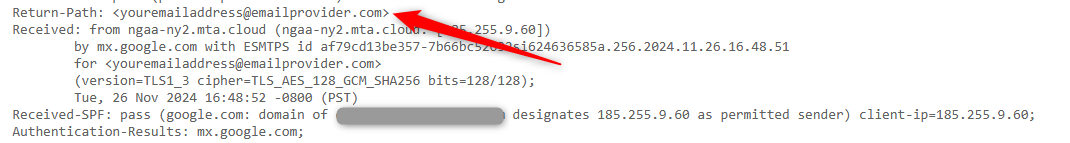
The first is the Sender Policy Framework (SPF), which works with some basic principles. Every email domain comes with a set of Domain Name System (DNS) records, which are used to direct traffic to the correct hosting server or computer. An SPF record works with the DNS record. When you send an email, the receiving service checks the SPF record of the sending domain to ensure the email comes from an authorized IP address. If the email originates from an IP address not listed in the SPF record, it may get flagged as spam or rejected outright.
Unfortunately, SPF alone doesn’t solve the problem. Someone needs to maintain SPF records properly at each domain, which doesn’t always happen. It’s also easy for scammers to work around this problem. When you receive an email, you might only see a name instead of an email address. Spammers fill in one email address for the actual name and another for the sending address that matches an SPF record. So, you won’t see it as spam, and neither will SPF.
Companies must also decide what to do with SPF results. Most often, they settle for letting emails through rather than risking the system not delivering a critical message. SPF doesn’t have a set of rules regarding what to do with the information; it just provides the results of a check.
To address these issues, Microsoft, Google, and other email service providers introduced the Domain-based Message Authentication, Reporting, and Conformance (DMARC) validation system. It works with SPF to create rules for what to do with emails flagged as potential spam. DMARC first checks the SPF scan. If that fails, it stops the message from going through unless it’s configured otherwise by an administrator.
Even if an SPF passes, DMARC then checks for alignment—ensuring that the email address in the “From” field matches the domain the email came from. Thanks to the widespread adoption of DMARC, we’ve seen a steady decrease in spoof emails.
What You Can Do About Self-Addressed Spam
Unfortunately, there’s no guaranteed way to prevent spammers from spoofing your address. Hopefully, the email system you use implements both SPF and DMARC, and you won’t see these targeted emails. They should go straight to spam. If your email provider gives you control of its spam options, you can make them more strict. Be aware that you might also lose some legitimate messages, so be sure to check your spam box often.
If you do get a spoofed message from yourself, ignore it. Don’t click any attachments or links, and don’t pay any demanded ransoms. Just mark it as spam or phishing, or outright delete it.
If you’re afraid your accounts have been compromised, lock them down for safety. Change your passwords, enable two-factor authentication, and make sure you don’t use the same password on any of your accounts. If you don’t trust your memory with so many passwords, we recommend using a password manager.
If you keep receiving spoofed emails from your own email or your contacts, consider switching to a different email service provider. For instance, Proton Mail tends to do a better job at filtering out spam compared to other service providers.